In the early days of the internet, communication usually happened unencrypted. In this time an email used to be as secure as a postcard. Everyone who had access to any point of the transfer was able to read along.
Only in the last few years, data communication started to be encrypted, fe. with SSL. But SSL only encrypts the transmission of the data, not the data itself.
There is generally speaking no guarantee that anyone of the involved email servers is actually using secure encryption methods. Also, email messages are stored unencrypted in the postboxes of providers. Often times postboxes had been compromised (“hacked”). Usually, hackers do not target to attack a single person. They rather try to generally find security leaks and take advantage of them. Security leaks can be weak password or weak systems for example.
In order to defend against that, it is possible to encrypt the whole email message instead of only encrypting the transfer. The standard PGP (“pretty good privacy”) allows it. Other than the name may suggest, this system is actually really safe instead of being “pretty good”. And thanks to OpenPGP it is also open-source and freely available.
Please feel free to skip the following paragraph if you don’t like things to be too technical. For our email encryption, PGP uses asymmetric key algorithms. The recipient (person A) of a message has a private key. It is needed to decrypt a message. The sender (person B) needs the public key of person A for the encryption of the message. Person A, the recipient, needs to transmit this public key to person B before encryption can happen. After that, person B will be able to encrypt and send a message with the public key of person A. As long as person A keeps its private key safely on its PC, only person A will be able to read its messages.
In order to send a message from person A to person B, person A needs the public key of person B.
If there are any doubts about a person really being who the person claims to be, a so called “handshake” can be performed. In practice, this means the exchange of security words away from keyboard. The security words can be transmitted on the phone or in real live. This makes the email conversation not only secure, but also reliable.
Honestly, this sounded complicated. And it actually used to be complicated for a long time. Thanks to a project called PEP (“Pretty Easy Privacy”) it got really easy now. PEP can be installed as an add-on for some email client programs and will take care of everything regarding encryption. This includes generating, attaching and importing of public keys and also generating a private key and decrypting incoming encrypted messages. If the conversational partners are using OpenPGP without PEP, it is still possible to communicate encrypted. Add-Ons with PEP like Enigmail are freely available for email clients like Thunderbird. There are also commercial extensions, for example for Outlook.
The following lines are supposed to show how you can encrypt your email conversations -completely free- with Thunderbird and the Add-On Enigmail with PEP. The following pictures have been made on a GNU/Linux-based operating system with Thunderbird 60.7.0 (64-bit). The operation can be different with other operating systems and software versions.
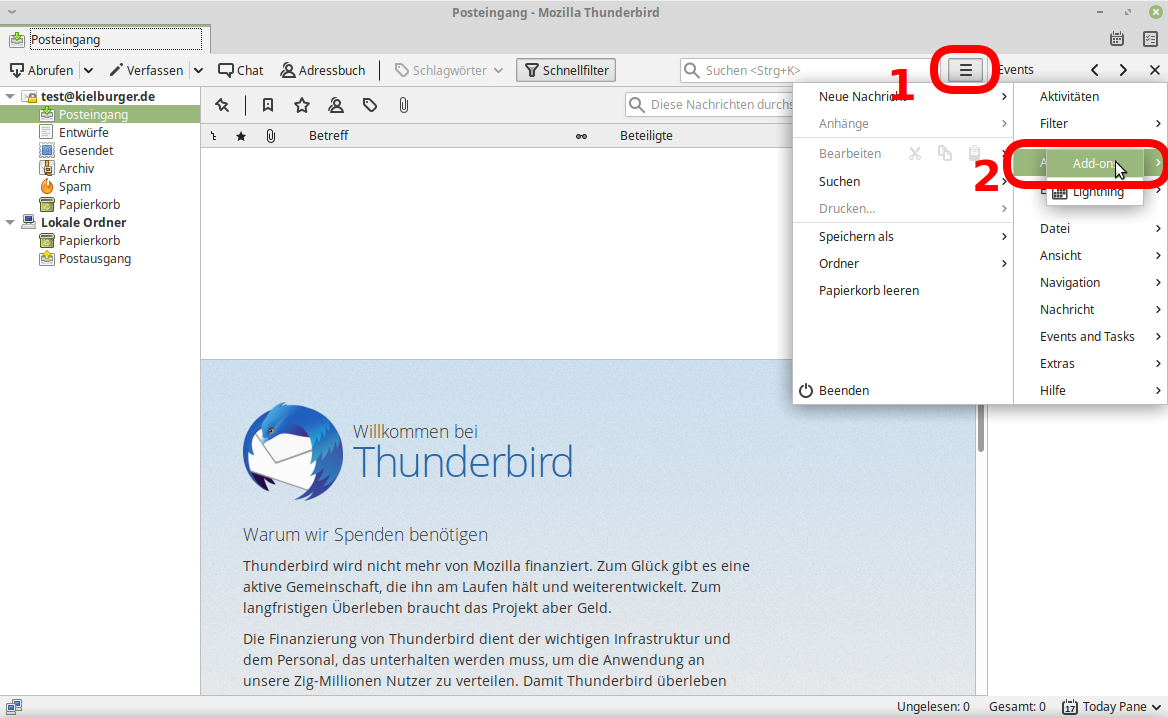
Step 1: Open Menu (1) in Thunderbird and click on Add-Ons twice (2).
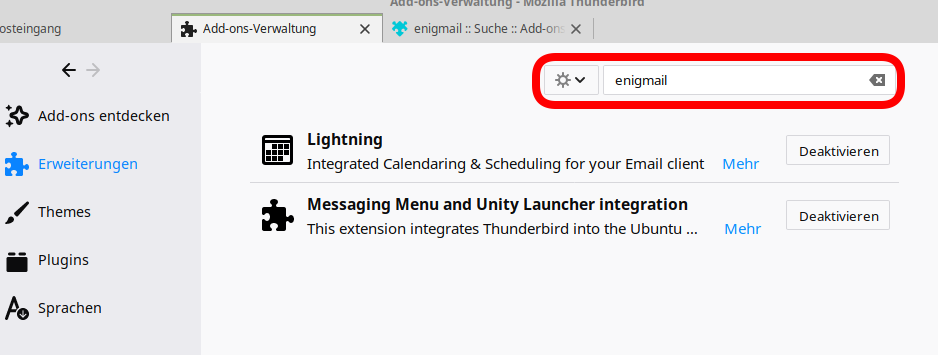
Step 2: Search for the Add-On “Enigmail”.
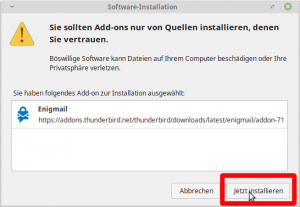
Step 3: Install Enigmail (self-explaining)

Enigmail automatically creates a private and a public key in the background. There is nothing to do for you. The picture just illustrates that a new key has been created.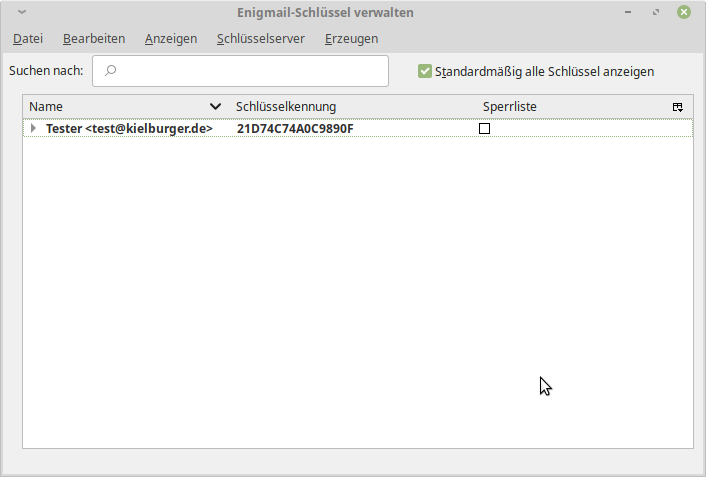
Step 4: Importing the first key
We receive an email from someone who is also using PGP-based encryption. Enigmail automatically recognizes that a public key is attached to the email. If we want to answer or send a regular email to this participant, it will be automatically encrypted.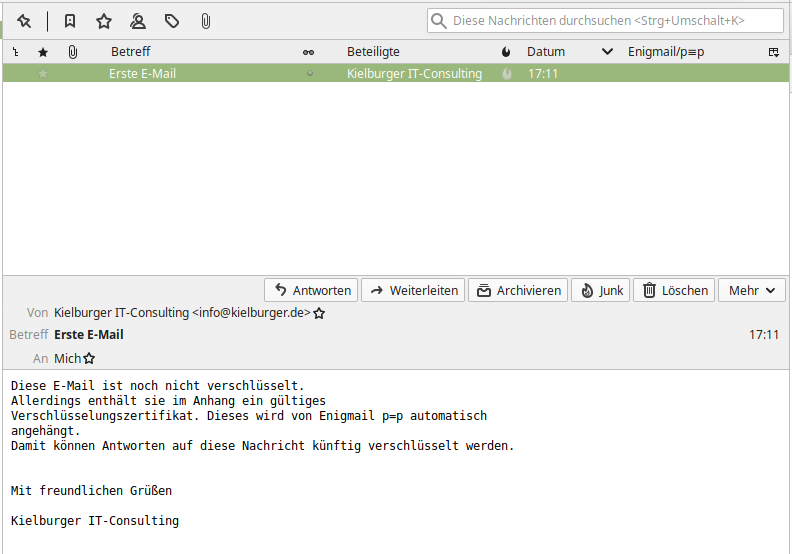
Step 5: Sending the first encrypted email and eventually performing a handshake
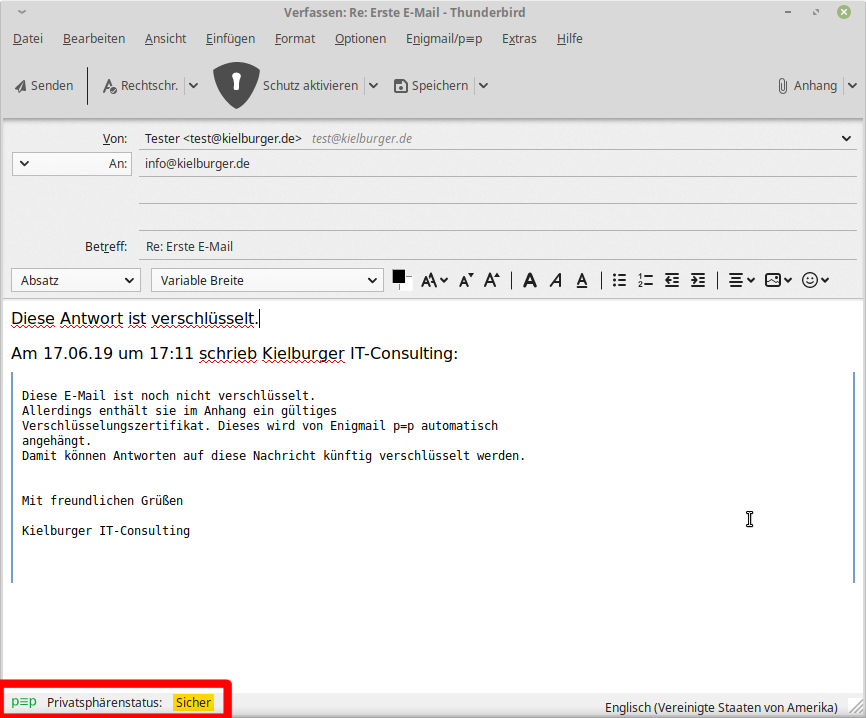
PEP shows, that this message is secure. This means, that right now we are sending this message encrypted. Our own public key will be automatically attached. Therefore the recipient will be able to encrypt its answer message.
Eventually we also want to secure the trust between us and the recipient of this email by performing a handshake. This is not mandatory, though.
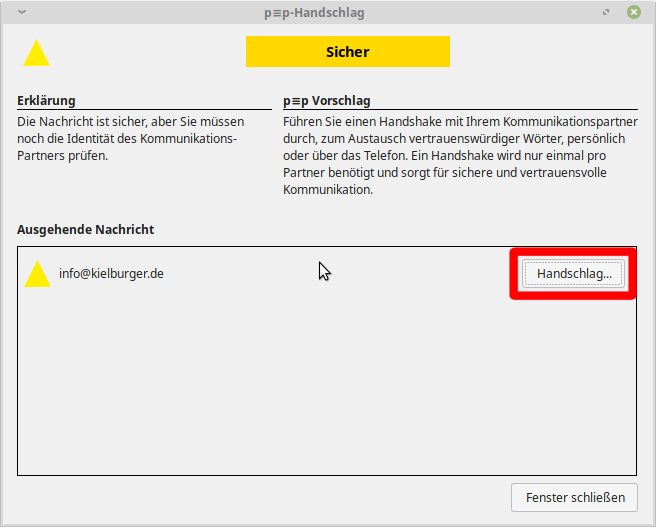
By clicking on the yellow-marked area “Secure” the handshake can be arranged. PEP will give self-explaining instructions about this. If you want to perform a handshake, it has to be re-done for each participant you are communicating with.
Done. We have just massively increased the security of our email conversations.
Hints:
- Even if the email itself is encrypted, the transmission should still be secured with SSL. Only by encrypting the transmission it can be assured that meta data and passwords are also transferred encrypted.
- If our interlocutor does not use any type of PGP/PEP/OpenPGP-encryption, we won’t be able to communicate encrypted with that person. It always takes two! Enigmail with PEP will always show you if a message will actually be sent encrypted.
- Whenever we receive an encrypted message, it can only be decrypted with our private key. Therefore it makes sense to have backup of our key that is stored secure and privately, fe. on an encrypted USB flash drive.
- Reading encrypted messages is generally only possible with an email client program like Thunderbird. Reading encrypted messages on the web, fe. at GMail or Hotmail is only possible with a few providers with browser add-ons. Not every provider allows reading encrypted messages and some do only with limitations.
Please be aware, that all of this informations and/or tutorials come without any type of warranty.



















 Deutsch
Deutsch